41 Man In The Middle Attack
Man wanted in Region machete attack, police say | Crime ... 24.01.2022 · GARY — A man was wanted Friday on charges he attacked another man with a machete last fall while they were drinking at an illegal alcohol establishment in Gary's Aetna section, police said ... How to perform a Man-in-the-middle (MITM) attack with Kali ... 25.03.2017 · Learn how to perform a Man in the middle attack with arpspoof, driftnet and urlsnarf in Kali Linux In this article, you will learn how to perform a MITM attack to a device that's connected in the same Wi-Fi networks as yours. Requirements. This article assumes that you know what is a network interface and you know to how to work with Kali Linux and the …
› blog › man-in-the-middle-attack-2Executing a Man-in-the-Middle Attack in just 15 Minutes ... Apr 29, 2021 · Obviously, you know that a Man-in-the-Middle attack occurs when a third-party places itself in the middle of a connection. And so that it can be easily understood, it’s usually presented in the simplest iteration possible—usually in the context of a public WiFi network.
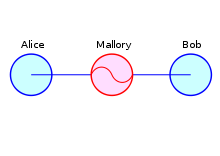
Man in the middle attack
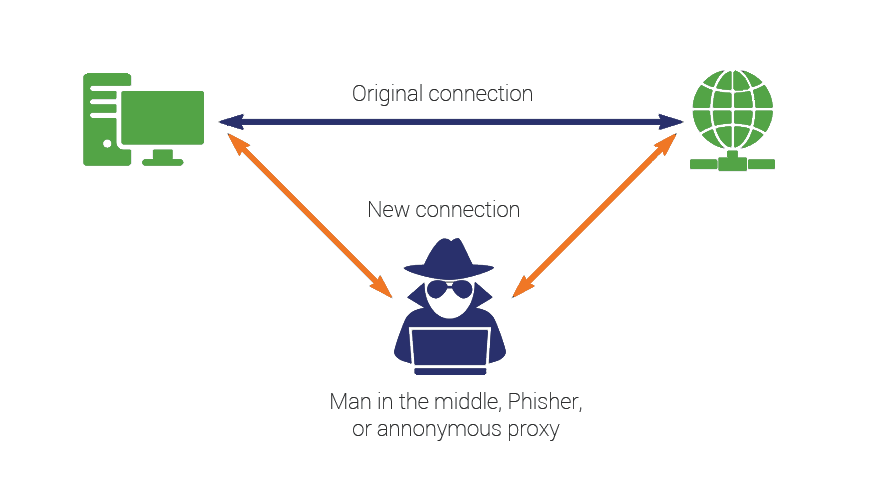
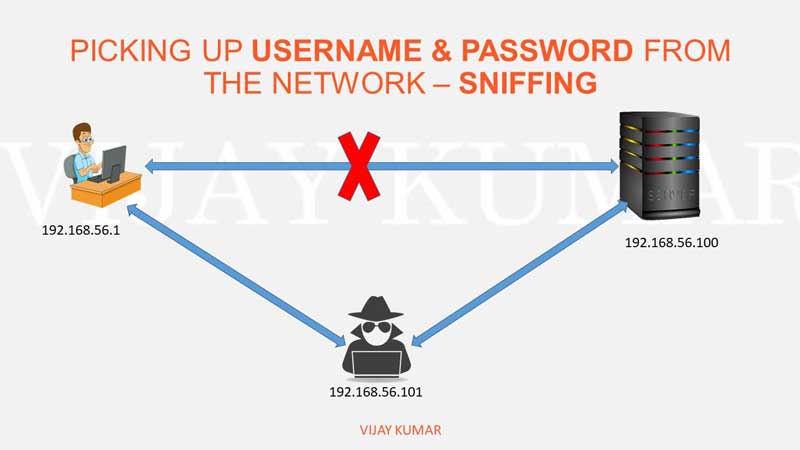
› kali-linux-man-in-theKali Linux Man in the Middle Attack Tutorial for Beginners 2021 Jun 24, 2021 · Man in the middle attack is the most popular and dangerous attack in Local Area Network. With the help of this attack, A hacker can capture username and password from the network. This article will cover man in the middle attack tutorial, definition, techniques, tools and prevention methods simple and easy examples. › Deal-with-a-Man-in-the-Middle-Attack3 Ways to Deal with a Man in the Middle Attack - wikiHow Jun 24, 2020 · The terminology man-in-the-middle attack (MTM) in internet security, is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is ... Man-in-the-browser - Wikipedia Man-in-the-browser (MITB, MitB, MIB, MiB), a form of Internet threat related to man-in-the-middle (MITM), is a proxy Trojan horse that infects a web browser by taking advantage of vulnerabilities in browser security to modify web pages, modify transaction content or insert additional transactions, all in a covert fashion invisible to both the user and host web application.
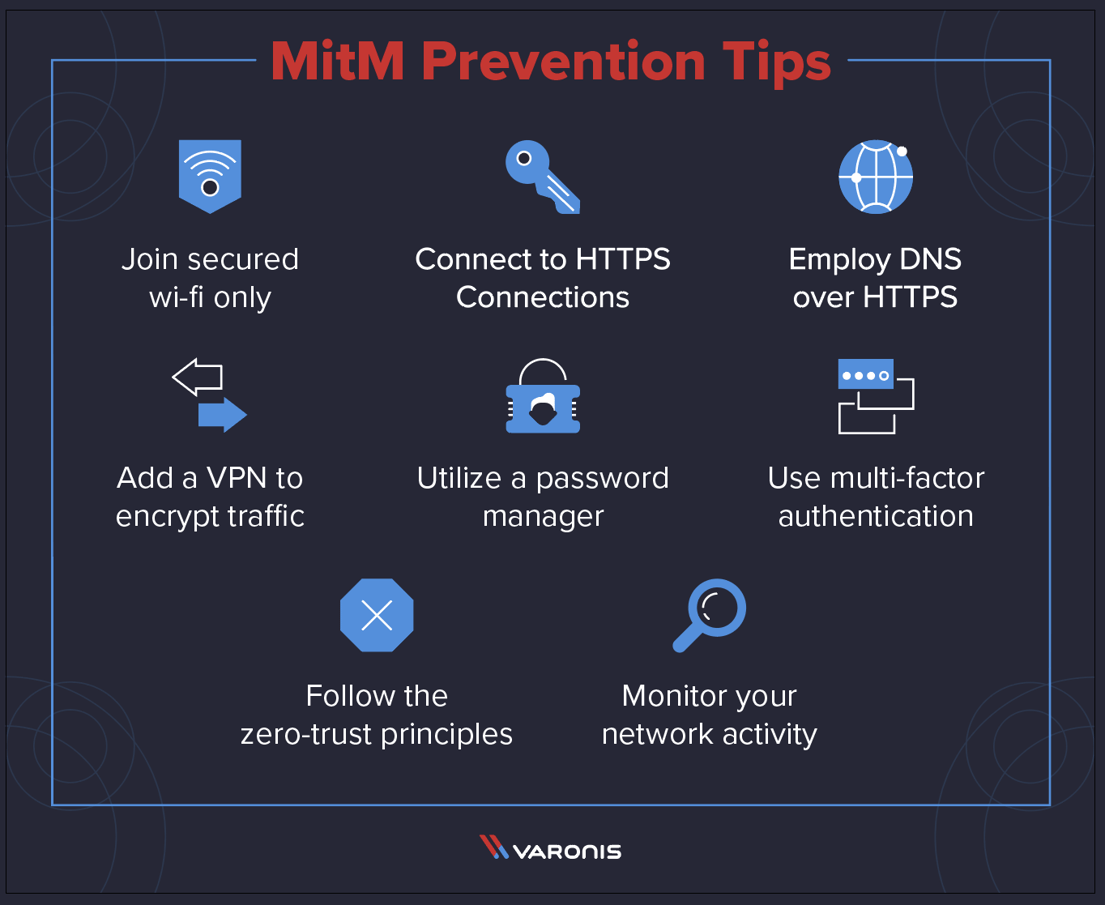
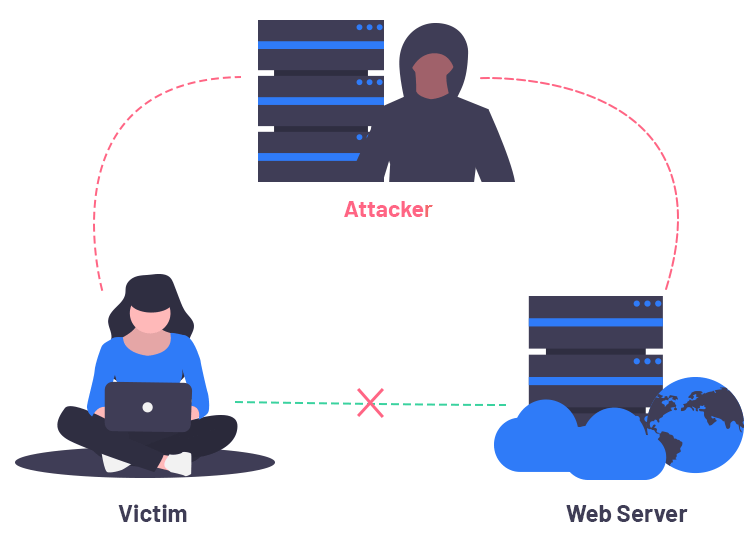
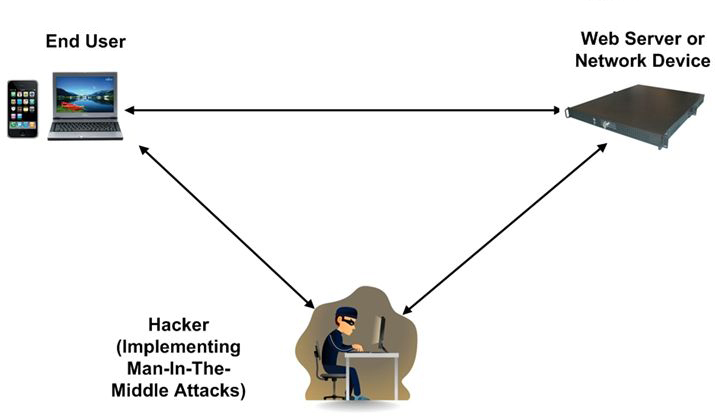
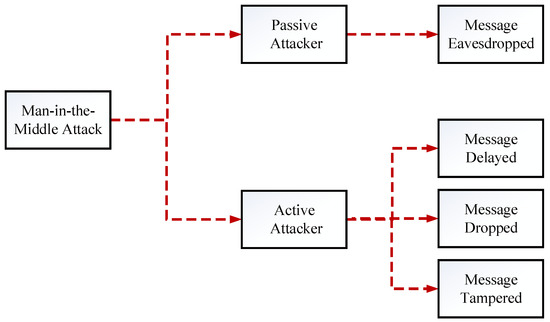
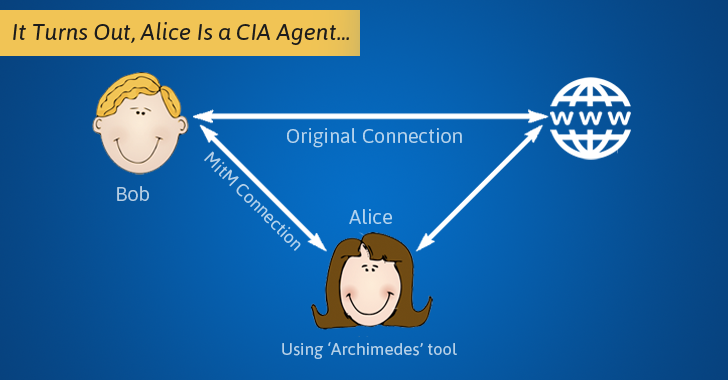
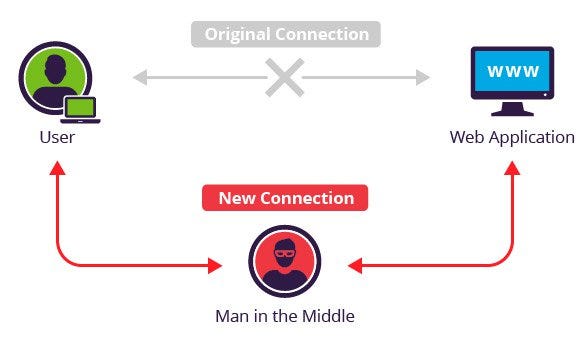
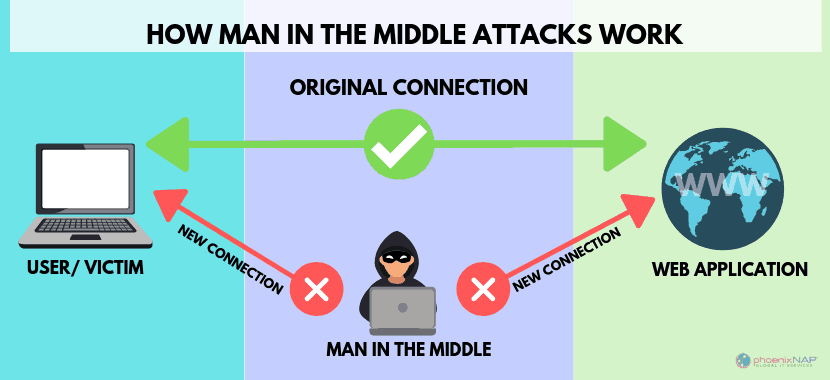
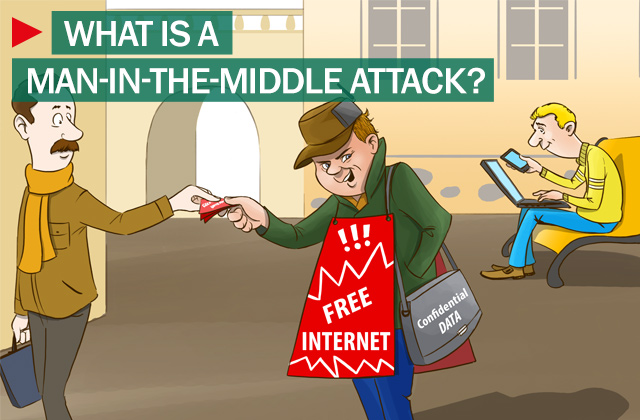
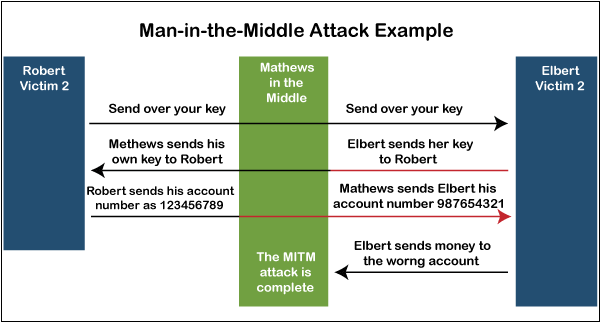
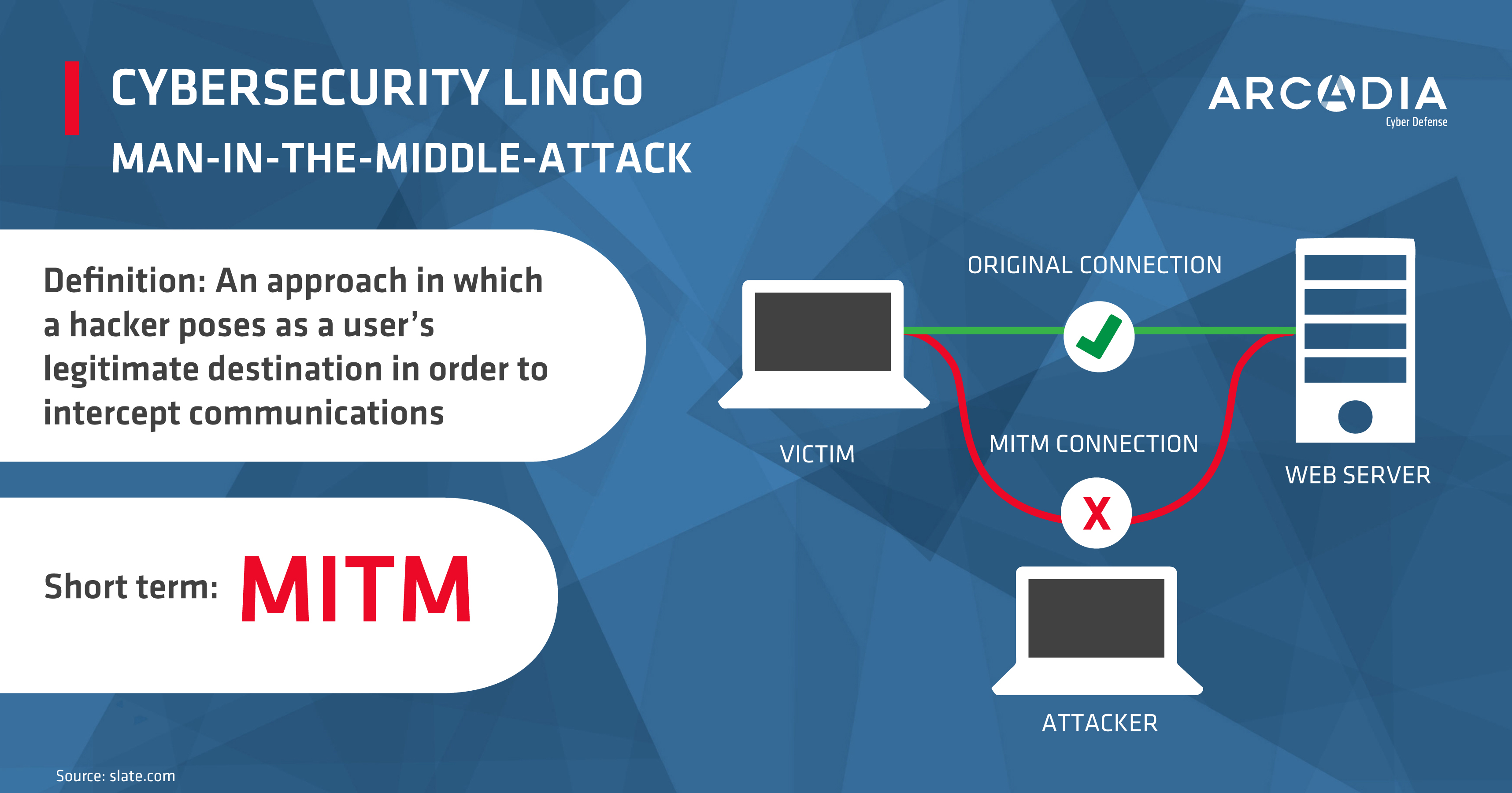
Man in the middle attack. › blog › man-in-the-middle-attackWhat Is a Man-in-the-Middle Attack and How Can It Be ... Oct 13, 2021 · A man-in-the-middle attack (MITM attack) is a cyber attack where an attacker relays and possibly alters communication between two parties who believe they are communicating directly. This allows the attacker to relay communication, listen in, and even modify what each party is saying. Man in the Middle (MITM) Attacks | Types, Techniques, and ... Man-in-the-middle attacks (MITM) are a common type of cybersecurity attack that allows attackers to eavesdrop on the communication between two targets. The attack takes place in between two legitimately communicating hosts, allowing the attacker to “listen” to a conversation they should normally not be able to listen to, hence the name “man-in-the-middle.” en.wikipedia.org › wiki › Man-in-the-middle_attackMan-in-the-middle attack - Wikipedia In cryptography and computer security, a man-in-the-middle, monster-in-the-middle, machine-in-the-middle, monkey-in-the-middle, meddler-in-the-middle (MITM) or person-in-the-middle (PITM) attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has ... Berlin U-Bahn attackers try to set homeless man on fire in ... Germany Berlin U-Bahn attackers try to set homeless man on fire in Christmas Eve attack. Just weeks after a subway attack triggered a national outcry, a …
us.norton.com › internetsecurity-wifi-what-is-aWhat is a man-in-the-middle attack? - Norton Mar 26, 2020 · A man-in-the-middle attack is like eavesdropping. When data is sent between a computer and a server, a cybercriminal can get in between and spy. A man-in-the-middle attack requires three players: the victim, the entity with which the victim is trying to communicate, and the “man in the middle” who’s intercepting the victim’s communications. › security › man-middle-attackMan in the Middle Attack: Tutorial & Examples | Veracode A man-in-the-middle attack is a type of eavesdropping attack, where attackers interrupt an existing conversation or data transfer. After inserting themselves in the "middle" of the transfer, the attackers pretend to be both legitimate participants. Beijing Olympics App Flaws Allow Man-in-the-Middle Attacks 19.01.2022 · If successful, an attacker launching a man-in-the-middle attack could gain access to sensitive information stored in the app. MY2022 uses encryption to protect users’ voice audio and files transfers. However, this encryption can be sidestepped due to two different vulnerabilities affecting how it handles data transport, according to Citizen Lab. Server responses can … Man-in-the-browser - Wikipedia Man-in-the-browser (MITB, MitB, MIB, MiB), a form of Internet threat related to man-in-the-middle (MITM), is a proxy Trojan horse that infects a web browser by taking advantage of vulnerabilities in browser security to modify web pages, modify transaction content or insert additional transactions, all in a covert fashion invisible to both the user and host web application.
› Deal-with-a-Man-in-the-Middle-Attack3 Ways to Deal with a Man in the Middle Attack - wikiHow Jun 24, 2020 · The terminology man-in-the-middle attack (MTM) in internet security, is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is ... › kali-linux-man-in-theKali Linux Man in the Middle Attack Tutorial for Beginners 2021 Jun 24, 2021 · Man in the middle attack is the most popular and dangerous attack in Local Area Network. With the help of this attack, A hacker can capture username and password from the network. This article will cover man in the middle attack tutorial, definition, techniques, tools and prevention methods simple and easy examples.
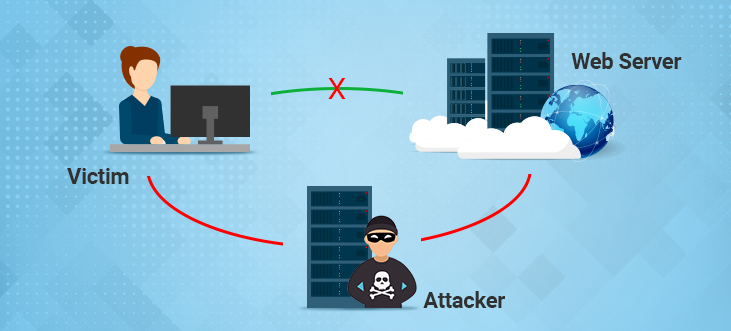
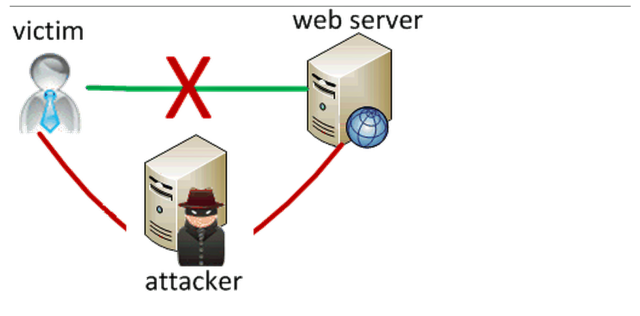
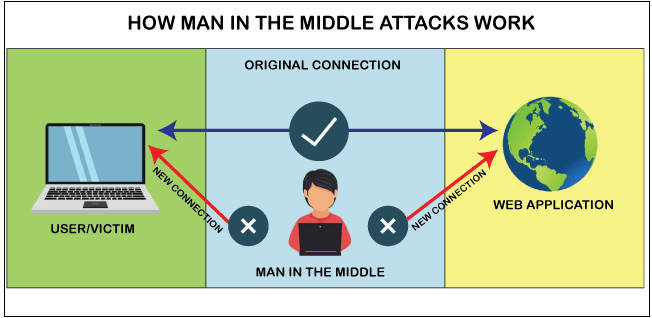
















%20Attack.jpg)





0 Response to "41 Man In The Middle Attack"
Post a Comment